ALOHA is a protocol for satellite and terrestrial radio transmissions. In pure Aloha, a user can transmit at any time but risks collisions with other users' messages. "Slotted Aloha" reduces the chance of collisions by dividing the channel into time slots and requiring that the user send only at the beginning of a time slot. Aloha was the basis for Ethernet, a local area network protocol.
Pure ALOHA
Graph of frames being sent from 4 different stations according to the pure ALOHA protocol with respect to time, with overlapping frames shaded to denote collision. The first version of the protocol (now called "Pure ALOHA", and the one implemented in ALOHAnet) was quite simple:
- If you have data to send, send the data
- If, while you are transmitting data, you receive any data from another station, there has been a message collision. All transmitting stations will need to try re sending "later".
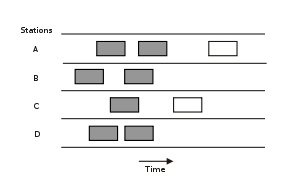 |
| Boxes indicate frames. Shaded boxes indicate frames which have collided. |
Note that the first step implies that Pure ALOHA does not check whether the channel is busy before transmitting. Since collisions can occur and data may have to be sent again, ALOHA cannot use 100% of the capacity of the communications channel. How long a station waits until it transmits, and the likelihood a collision occurs are interrelated, and both effect how efficiently the channel can be used. This means that the concept of "transmit later" is a critical aspect: the quality of the backoff scheme chosen significantly influences the efficiency of the protocol, the ultimate channel capacity, and the predictability of its behavior.
Slotted ALOHA
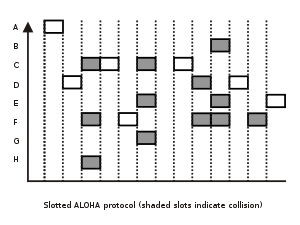
An improvement to the original ALOHA protocol was "Slotted ALOHA", which introduced discrete time slots and increased the maximum throughput.A station can send only at the beginning of a time slot, and thus collisions are reduced. In this case, we only need to worry about the transmission-attempts within 1 frame-time and not 2 consecutive frame-times, since collisions can only occur during each time slot.
Thus, the probability of there being zero transmission-attempts in a single time slot is:
Prob_{slotted} = e^{-G}
the probability of k packets is:
Prob_{slotted} k = e^{-G} ( 1 - e^{-G} )^{k-1}
The throughput is:
S_{slotted}=Ge^{-G}
The maximum throughput is 1/e frames per frame-time (reached when G = 1), which is approximately 0.368 frames per frame-time, or 36.8%. Slotted ALOHA is used in low-data-rate tactical satellite communications networks by military forces, in subscriber-based satellite communications networks, mobile telephony call setup, set-top box communications and in the contact less RFID technologies.
The use of a random-access channel in ALOHAnet led to the development of carrier sense multiple access (CSMA), a "listen before send" random-access protocol that can be used when all nodes send and receive on the same channel. The first implementation of CSMA was Ethernet. CSMA in radio channels was extensively modeled.[11] The AX.25 packet radio protocol is based on the CSMA approach with collision recovery,[12] based on the experience gained from ALOHAnet.
ALOHA and the other random-access protocols have an inherent variability in their throughput and delay performance characteristics. For this reason, applications which need highly deterministic load behavior sometimes used polling or token-passing schemes (such as token ring) instead of contention systems. For instance ARCNET was popular in embedded data applications in the 1980 network.
Script for wired connection: